Vulnerability Assessment Implementation for Risk Mitigation Considerations
Review Business Documents
- Review Corporate Strategy and Operations Documents to validate goal to execution probability/capability, as related to the enterprise and/or specific operational areas.
Interview Business Leadership
- Interview Corporate and Departmental Leadership to discover the perceived vulnerabilities across the organization, people, process, technology, and programs, as they relate to the enterprise and/or specific operational areas.
Business Risks and Assumptions Analysis
- Generate a comprehensive Risks and Assumptions Analysis delivered via a collaborative session with leadership, to establish the next steps toward mitigating the now identifiable vulnerabilities.
Why a Vulnerability Assessment Is Important for Risk Planning and Mitigation Prior to Change
Being proactive to avoid risk is a mission critical activity in any organization that values business continuity. The overt risks associated with enterprise and/or specific operational areas of business today, are more advanced than ever before. Before taking any corrective action on the organization, people, process, technology, and programs that make up the DNA of your company, it is imperative to identify the goal/value correlation, and thus, a Vulnerability Assessment “pre-step” to ensure the tightest alignment to the organization’s goals, is critical. Vulnerability assessment is not just a technical exercise; it’s a mission-critical component for businesses of all sizes.
-
Risk Identification and Prioritization
- Business Continuity: Vulnerability assessments help identify weaknesses in your systems, applications, and infrastructure. By understanding these vulnerabilities, you can prioritize remediation efforts effectively.
- Financial Impact: Addressing vulnerabilities before they are exploited prevents financial losses due to data breaches, downtime, or regulatory fines.
-
Preventing Data Breaches and Unauthorized Access
- Confidential Information: Vulnerabilities can lead to unauthorized access to sensitive data—customer records, financial information, intellectual property, and trade secrets. A breach can tarnish your reputation and result in legal consequences.
- Compliance: Many industries have compliance requirements (e.g., GDPR, HIPAA, PCI DSS). Regular vulnerability assessments ensure adherence to these standards.
-
Mitigating Cybersecurity Risks
- Proactive Defense: Assessments allow you to proactively address risks. Waiting for an attack to occur is risky and costly.
- Third-Party Risks: Assessing vulnerabilities in third-party software or services is crucial. Your business ecosystem is only as secure as its weakest link.
-
Operational Resilience
- Business Operations: Vulnerabilities can disrupt operations, leading to financial losses and customer dissatisfaction. Assessments help maintain operational resilience.
- Supply Chain: Assessing vulnerabilities in supply chain partners ensures a robust ecosystem.
-
Regulatory Compliance and Audits
- Audits and Assessments: Regulatory bodies and auditors expect organizations to demonstrate due diligence in managing vulnerabilities. Regular assessments provide evidence of compliance.
- Risk Management Frameworks: Vulnerability assessments align with risk management frameworks (e.g., NIST, ISO 27001).
-
Staying Ahead of Threat Actors
- Threat Landscape: Cyber threats evolve rapidly. Assessments keep you informed about emerging vulnerabilities and attack vectors.
- Zero-Day Vulnerabilities: Identifying zero-day vulnerabilities (before they are publicly disclosed) allows proactive patching or mitigation.
Summary
Vulnerability assessments are like health check-ups for your business. They diagnose issues, prescribe remedies, and ensure your organization stays fit to face the ever-changing threat landscape. Remember, investing in vulnerability assessments is not an expense; it’s an investment in your business’s resilience and longevity. If you haven’t already, consider implementing a robust vulnerability assessment program—it’s mission-critical.
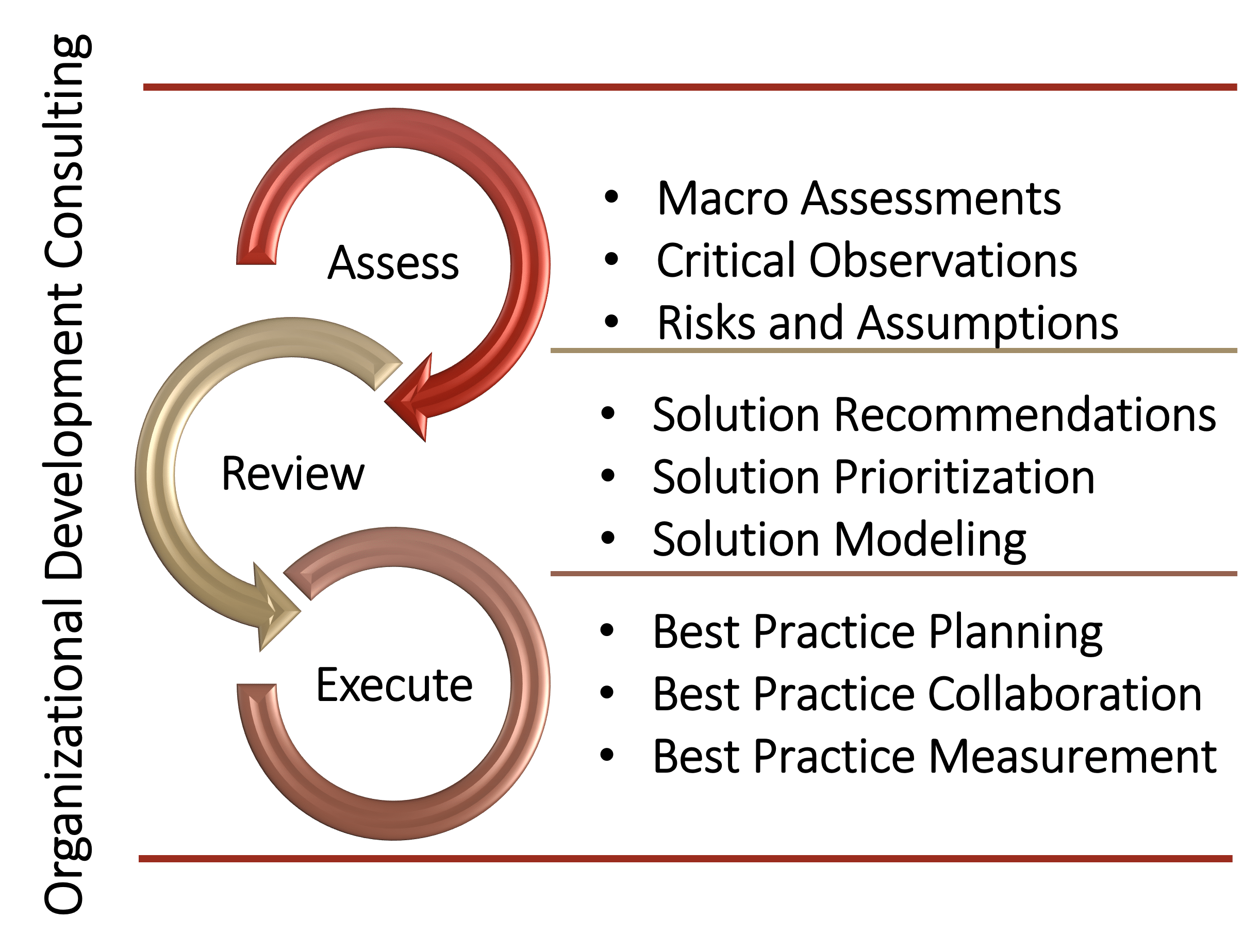
Organizational Development Consulting
Client-Centric Engagement Model
Each solution found in our catalog can be scaled to meet your organization's needs. Consulting engagements are built on a collaborative three-step process of Assess, Review, and Execute stage gates. This model provides a high value and collaborative approach that allows organizations to measure ROI, performance, and continuous improvement throughout the entire engagement. Our executive level team of consultants will provide actionable and practical recommendations that can be implemented via our collaborative approach to the partnership.
For the Enterprise
- Experience personalized service at scale. AMS has a global reach with the highest degree of expertise across a range of Fortune 500 companies, Government agencies and Global 2000 organizations.
For the Emerging and Middle-Market
- Experience the entrepreneurial spirt that our firm is founded on with a unique blend of expertise to accommodate the unique needs of smaller organizations.
Customize your Consulting Experience
- Align subject matter experts with your industry, region, and culture
- Support solutions with correlating Research
- Accelerate Individual Growth with Performance Coaching
- Supplement solutions with Professional Development Training
- Review Solution Briefings
- Integrate Digital Resources – Thought Leader Interviews – Insights Podcast
Join the ranks of leading organizations that have partnered with AMS to drive innovation, improve performance, and achieve sustainable success. Let’s transform together, your journey to excellence starts here.